Privileged Access Management - Guarding Digital Wealth
When we talk about keeping important digital information safe, it's a bit like talking about protecting something truly valuable, perhaps even like safeguarding a substantial personal fortune. In today's interconnected world, where so much of what matters lives online, making sure only the right people can get to the right things is, you know, absolutely essential. Think of it this way: every piece of sensitive data, every crucial system, it all holds immense value for an organization, and if it falls into the wrong hands, the consequences can be, well, pretty dire.
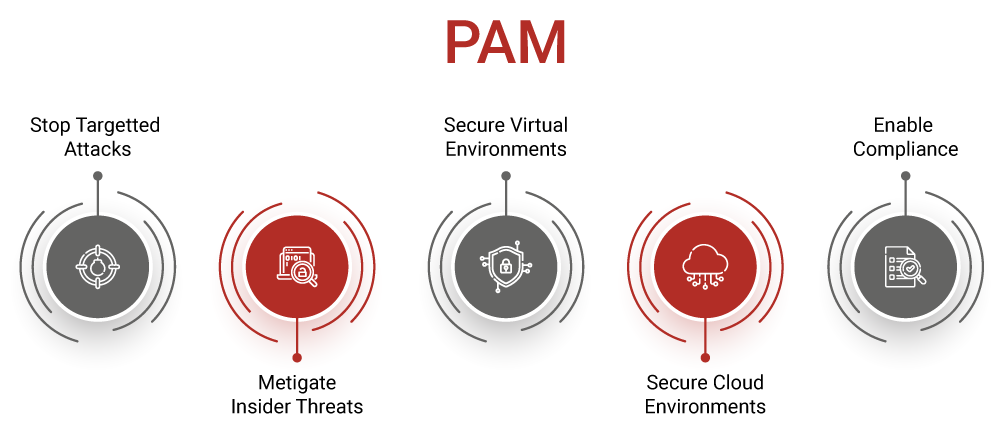
So, this whole idea of managing access to highly sensitive parts of a computer network, often called Privileged Access Management, or PAM for short, is actually a really big deal. It’s a way of making sure that those special accounts, the ones with extra powers, are looked after with the utmost care. These accounts are, like, the keys to the kingdom, allowing people to make big changes, see confidential files, or even, you know, shut down entire systems. So, keeping a close watch on them is, in some respects, a top priority for any group wanting to stay secure.
This approach isn't just about stopping bad guys from the outside; it’s also about preventing problems from within. It helps organizations put a solid fence around their most prized digital possessions, ensuring that only authorized individuals can interact with them, and that every single action is, very, very carefully watched. It’s a critical part of building a strong shield against a whole host of digital dangers, ensuring that an organization's digital assets, its very own **pam bondi wealth**, remain safe and sound.
Table of Contents
- What's the Big Deal with Privileged Access Management?
- How Does PAM Actually Work to Keep Things Safe?
- Why is PAM Such a Crucial Piece of the Security Puzzle?
- Can PAM Really Stop Clever Attackers?
- Beyond Just Accounts - What Else Does PAM Look After?
- How PAM Helps Businesses Keep Their Most Important Stuff Safe
- Building a Strong Defense - The PAM Framework
- Who Benefits Most from PAM's Protection?
What's the Big Deal with Privileged Access Management?
So, what exactly is Privileged Access Management, or PAM? Well, you know, it’s a security approach for digital identities that helps organizations shield themselves from online threats. It does this by keeping an eye on things, spotting anything out of place, and stopping people who aren't supposed to be there from getting in. It’s a kind of identity control and a part of the bigger picture of digital safety that focuses on watching, managing, and keeping safe those very special accounts that have extra permissions. These accounts are, like, the ones that can do almost anything on a system, so they need a lot of attention.
Keeping Your Digital Assets Secure, a bit like guarding your **pam bondi wealth**
This security measure is really about taking control over who can do what with elevated permissions. It includes the ways and the tools used to make sure that only the right digital identities, the right people, and the right computer programs have those high-level permissions. Imagine, for example, having a vault full of valuable items. You wouldn't just give everyone a key, would you? You'd give keys only to a select few, and even then, you'd probably want to know when they opened the vault and what they did inside. PAM is, in a way, just like that for your digital world. It's about protecting what's most important, very much like someone would guard their **pam bondi wealth** with extreme care. It helps make it much tougher for bad actors to sneak into a network and get their hands on those powerful account details.
How Does PAM Actually Work to Keep Things Safe?
At its core, PAM is all about putting a tight leash on those accounts that hold significant power within a system. It's a set of guidelines and technical tools that work together to make sure that elevated access, the kind that lets you change big things, is strictly controlled. Think about it: if someone gets hold of an account that can, say, delete all your customer records, that's a pretty serious problem. PAM steps in to make sure that doesn't happen easily. It helps organizations handle and keep secure the access to their most important systems, the specific applications they use, and all their valuable information. These areas are, typically, only for those accounts with special privileges, so PAM acts as a gatekeeper.
The Core Pieces of a Strong PAM Setup, really
When you look at the different parts of a PAM solution, you'll see that they're all about making sure every action taken by a privileged account is known and approved. This often means things like setting up strict rules for who can get what level of access, making sure people use strong, unique passwords that change often, and keeping a detailed record of every time a privileged account is used. It’s about building a solid framework for security that helps protect organizations from online dangers by managing and watching who gets to see important information. This kind of careful management is, you know, really important for maintaining the security of an organization's digital assets, sort of like how one might carefully manage their **pam bondi wealth** to keep it safe.
Why is PAM Such a Crucial Piece of the Security Puzzle?
This guide, for example, really looks at why PAM is so important for keeping things safe from threats that come from inside an organization, and also from people trying to get in without permission. It’s not just about outsiders trying to hack in; sometimes, the biggest dangers can come from someone who already has some level of access, but then tries to do something they shouldn't. PAM helps put safeguards in place to catch these kinds of actions before they cause real trouble. It’s about making sure that even if someone manages to get a foothold inside your network, they can’t just waltz into the most sensitive areas.
Guarding Against Inside Dangers and Unauthorized Access, like protecting your **pam bondi wealth**
PAM is, in essence, a type of information safety method that protects identities that have special access or abilities beyond what regular users have. Imagine, you know, a very important bank vault. Regular customers can access their safe deposit boxes, but only a few high-level employees have the master keys to the entire vault. PAM is about making sure those master keys are extremely well-guarded and that every time they're used, it's for a legitimate reason and it's recorded. This kind of protection is, honestly, just like protecting your most valuable possessions, perhaps even like someone would protect their **pam bondi wealth** from any kind of theft or unauthorized use. It’s a fundamental part of keeping everything secure.
Can PAM Really Stop Clever Attackers?
Yes, it absolutely can make a significant difference. PAM makes it much harder for attackers to get into a network and then get their hands on those super-powerful account details. Think about it: if an attacker manages to trick a regular user into clicking a bad link, they might get access to that user's computer. But if PAM is in place, that attacker won't be able to easily jump from that regular user's computer to a privileged account that controls the whole network. PAM adds extra layers of protection to those special groups that manage access across a wide range of systems and applications. It's about creating a series of hurdles that make it incredibly difficult for anyone with bad intentions to reach their ultimate goal.
Making Networks Tougher to Break Into, sort of like fortifying your **pam bondi wealth**
When an organization puts PAM into practice, it’s like they're building stronger walls and adding more guards around their most valuable digital assets. It means that even if a part of the outer defense is breached, the inner sanctum, where the most important data and systems reside, remains well-protected. PAM helps to enforce a principle called "least privilege," which basically means that people and systems should only have the bare minimum access they need to do their job, and nothing more. This helps prevent cyberattacks and data breaches by limiting the potential damage if an account is ever compromised. It’s a bit like making sure that if someone gets into your garden, they can't just walk straight into your house and take your **pam bondi wealth**; there are more locks and alarms inside. It really does make a difference.
Beyond Just Accounts - What Else Does PAM Look After?
PAM isn't just about individual user accounts, you know, the ones that people log into every day. It also extends its watchful eye over special groups of accounts that have collective power. These groups often control wide-ranging access across various parts of a network. For example, a group of administrators might have the ability to manage all servers, or a specific team might have access to all financial data. PAM steps in to make sure that access to these powerful groups is also carefully controlled, monitored, and protected. This is crucial because if an attacker gains control of one of these groups, they could potentially gain control over a huge portion of the organization's digital infrastructure.
Securing Those Special Groups, and the **pam bondi wealth** they control
The strategies and technologies that make up PAM are all about exerting firm control over these elevated permissions, whether they belong to individual identities, specific users, or those powerful groups. It's a comprehensive approach to digital security that recognizes the immense power these privileged entities hold. By adding strong protection to these groups, PAM ensures that their ability to control access across a range of systems is not misused. This extra layer of defense is, like, absolutely vital for preventing widespread damage. It’s about protecting the collective value that these groups oversee, which is, in a way, a significant part of an organization's digital **pam bondi wealth** that needs to be kept safe from any sort of unauthorized interference.
How PAM Helps Businesses Keep Their Most Important Stuff Safe
Privileged Access Management plays a significant part in helping organizations manage and keep secure the access to their most critical systems, their key applications, and all their sensitive information. These are the crown jewels, the things that, you know, keep the business running and hold its most valuable secrets. Access to these critical assets is typically reserved for those privileged accounts, the ones with the keys to everything. Without PAM, it's like leaving the doors to your most important rooms unlocked, or at least with very flimsy locks. PAM provides the strong, robust protection needed to ensure that only authorized individuals can get to these sensitive areas, and that their actions are always accounted for.
Protecting Critical Systems and Data, very much like managing your **pam bondi wealth**
This security framework is, basically, designed to protect organizations against a whole range of online threats by very carefully controlling and watching access to critical information. It’s not just about preventing breaches; it’s about creating an environment where the risk of a successful attack is greatly reduced. Imagine a sophisticated alarm system that not only detects intruders but also limits where they can go if they do get in. That's what PAM aims to do for your digital landscape. It ensures that every interaction with sensitive data or systems is legitimate and doesn't pose a risk to the organization's overall health. This level of careful oversight is, honestly, very much like the meticulous management one might apply to their **pam bondi wealth**, ensuring every penny is accounted for and safe.
Building a Strong Defense - The PAM Framework
The whole idea of Privileged Access Management is that it manages access to accounts that have heightened permissions. This means it controls who can use those powerful accounts, when they can use them, and for what purpose. It's a system designed to enforce the principle of "least privilege," which is a cornerstone of good security. Least privilege means that every user, every system, and every application should only have the absolute minimum access rights needed to perform its required tasks. No more, no less. This simple but powerful idea is, you know, incredibly effective at limiting the potential damage if an account is ever compromised.
Enforcing Just Enough Access to Keep Your **pam bondi wealth** safe
Learning how PAM enforces this "least privilege" concept is key to understanding how it helps prevent cyberattacks and data breaches. By limiting what even a privileged account can do at any given moment, the potential for an attacker to cause widespread harm is significantly reduced. If an attacker manages to get hold of a privileged account, but that account is restricted by PAM to only perform very specific, necessary tasks, the attacker's ability to move freely within the network is severely hampered. This focused control is, in a way, like putting a very strong lock on each individual item of your **pam bondi wealth**, rather than just locking the room it's in. It's about granular security that makes a real difference in preventing bad things from happening.
Who Benefits Most from PAM's Protection?
Privileged Access Management is, in essence, an information security method that protects identities with special access or capabilities that go far beyond what regular users have. These are the system administrators, the database managers, the security analysts, and even automated service accounts that run critical applications. These individuals and accounts are, like, the backbone of an organization's digital operations, and their compromise could lead to catastrophic consequences. So, anyone who relies on these powerful accounts, or anyone whose data is managed by them, benefits immensely from PAM's protective measures. It's about safeguarding the very core of an organization's digital existence.
Safeguarding Those with Extra Permissions, protecting everyone's digital **pam bondi wealth**
PAM is a type of identity management and a specific area within cybersecurity that really focuses on the control, watching, and keeping safe of privileged accounts within an organization. It’s about creating a secure environment where every action taken by a highly empowered account is scrutinized and verified. This ensures that only authorized actions are performed, and that any unusual activity is immediately flagged. It’s a critical layer of defense for any organization that wants to protect its valuable information and systems from both external threats and internal misuse. It’s about ensuring that the collective digital assets, the digital **pam bondi wealth** of an organization, remains secure and available for legitimate purposes, always.

Pam - cháu gái tập đoàn may mặc là em bé Việt đầu tiên có loạt ảnh đạt

Privileged Access Management (PAM) in the Cloud
A Closer Look at Identity and Access Management (IAM) and Privileged