PAM In The Office: Safeguarding Your Critical Digital Assets
In today's interconnected digital landscape, the security of an organization's most valuable assets hinges on robust cybersecurity measures. One of the most critical, yet often misunderstood, pillars of this defense is Privileged Access Management (PAM). While the phrase "PAM in the office" might conjure images of a beloved TV show character for some, in the realm of cybersecurity, it refers to a sophisticated and indispensable framework designed to protect the very core of an organization's digital infrastructure. This article delves deep into what PAM truly means, why it's non-negotiable for any modern "office" or enterprise, and how it acts as a bulwark against the ever-evolving tide of cyberthreats.
Every organization, regardless of its size or industry, possesses critical systems, sensitive data, and applications that are the lifeblood of its operations. Access to these vital resources is typically granted to a select few – individuals with elevated permissions, often referred to as "privileged accounts." These accounts, by their very nature, represent a significant security risk if compromised. Privileged Access Management (PAM) is precisely the solution engineered to mitigate this risk, ensuring that only authorized personnel can access critical systems, under monitored conditions, thereby preventing unauthorized access and potential breaches that could cripple an organization. Understanding and implementing PAM is not just a best practice; it's a fundamental requirement for maintaining digital integrity and trust.
Table of Contents
- What is Privileged Access Management (PAM)?
- Why PAM is Crucial for "The Office" Environment
- Core Components of a Robust PAM Solution
- PAM's Role in Preventing Cyberattacks and Breaches
- Implementing PAM: Best Practices for Your Office
- The Future of Privileged Access Management in the Office
- Common Misconceptions About PAM
- Real-World Impact: Why PAM Matters for Every Organization
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized access. More specifically, PAM is a type of identity management and a branch of cybersecurity that focuses on the control, monitoring, and protection of privileged accounts within an organization. It encompasses the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for identities, users, and processes.
At its core, PAM manages access to accounts with heightened permissions. These "privileged accounts" are not just limited to IT administrators. They can include:
- Administrator Accounts: Accounts with full control over operating systems, applications, and databases.
- Root Accounts: On Linux/Unix systems, equivalent to administrator.
- Service Accounts: Used by applications or services to interact with other systems.
- Emergency Accounts (Break-Glass Accounts): Used for urgent access during system failures.
- Business Privileged Accounts: Accounts with access to sensitive financial data, HR records, or intellectual property.
The goal of PAM is to secure these powerful accounts, as they represent the keys to the kingdom. If a cybercriminal gains control of a privileged account, they can bypass security controls, steal sensitive data, deploy malware, or even shut down critical infrastructure. PAM makes it harder for attackers to penetrate a network and obtain privileged account access, significantly reducing the attack surface.
Why PAM is Crucial for "The Office" Environment
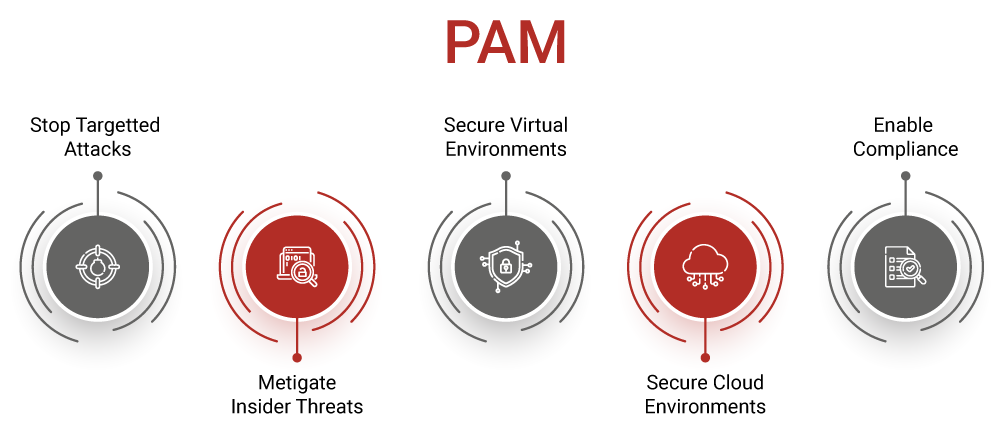
In any modern "office" or corporate setting, the digital perimeter is constantly under siege. From sophisticated nation-state attacks to opportunistic ransomware, the threats are relentless. This is where the importance of PAM in protecting against insider threats and unauthorized access becomes profoundly clear. A significant percentage of data breaches involve compromised privileged credentials, either through external attacks or malicious insider activity. Without PAM, an organization is left vulnerable.
Consider the typical flow of operations in an office: employees access various systems, IT staff manage servers, and contractors might temporarily need access to specific applications. Each of these interactions creates potential entry points for attackers. PAM adds protection to privileged groups that control access across a range of systems, ensuring that even if an attacker manages to breach the initial defenses, their ability to escalate privileges and move laterally within the network is severely hampered. It's about containing the damage and preventing a small crack from becoming a catastrophic collapse.
Furthermore, regulatory compliance (like GDPR, HIPAA, PCI DSS) often mandates strict controls over access to sensitive data. PAM solutions provide the necessary audit trails and enforcement mechanisms to meet these stringent requirements, helping organizations avoid hefty fines and reputational damage. It's not just about security; it's about governance and accountability.
Core Components of a Robust PAM Solution
A comprehensive Privileged Access Management solution is not a single tool but rather a suite of integrated capabilities designed to provide granular control and visibility over privileged accounts. To effectively safeguard identities with special access or capabilities beyond regular users, PAM solutions typically include several key components and adhere to best practices.
Centralized Management and Control
One of the foundational elements of PAM is the ability to centralize the management and control of all privileged accounts. This means consolidating credentials, policies, and access requests into a single, secure platform. Instead of privileged users directly logging into critical systems with shared or hardcoded credentials, they access these systems through the PAM solution. This helps organizations manage and secure access to their most critical systems, applications, and data, which are typically reserved for privileged accounts. Centralization simplifies auditing, streamlines provisioning and de-provisioning, and enforces consistent security policies across the entire IT estate.
Session Monitoring and Recording
Beyond simply granting or denying access, a robust PAM solution actively monitors and records privileged sessions. This means every action taken by a privileged user – every command entered, every file accessed, every configuration changed – is logged and can be replayed. This capability is crucial for forensic analysis in the event of a breach, for compliance audits, and for identifying suspicious behavior in real-time. By monitoring, detecting, and preventing unauthorized activities, organizations gain unprecedented visibility into their most sensitive operations, transforming accountability.
Just-in-Time Access and Least Privilege
The principle of "least privilege" is a cornerstone of effective cybersecurity, and PAM enforces it rigorously. This principle dictates that users should only be granted the minimum level of access necessary to perform their specific job functions, and only for the duration required. PAM solutions facilitate this by enabling "just-in-time" (JIT) access, where elevated permissions are granted only when explicitly requested and approved, and then automatically revoked after a set period or once the task is completed. Learn how PAM enforces least privilege to prevent cyberattacks & breaches. This significantly reduces the window of opportunity for attackers, as privileged access is not persistent, making it harder for them to exploit compromised credentials.
PAM's Role in Preventing Cyberattacks and Breaches
Privileged Access Management (PAM) is a security framework designed to protect organizations against cyberthreats by controlling and monitoring access to critical information. Its effectiveness stems from its ability to address the weakest link in many security postures: the privileged account. When an attacker gains control of a privileged account, they essentially gain full control over the targeted system or network. PAM directly counteracts this by making such an acquisition incredibly difficult and, if it occurs, quickly detectable.
For instance, PAM solutions often implement strong password management, rotating complex passwords for privileged accounts automatically, eliminating human error or weak password practices. They also introduce multi-factor authentication (MFA) for privileged access, adding another layer of security beyond just a password. By safeguarding identities with special access or capabilities beyond regular users, PAM significantly reduces the risk of credential theft, lateral movement by attackers, and insider threats. It acts as a gatekeeper, ensuring that even if a general user account is compromised, the attacker cannot easily elevate their privileges to access sensitive systems. This proactive defense mechanism is vital in today's threat landscape where sophisticated attacks often target privileged credentials as their primary objective.
Implementing PAM: Best Practices for Your Office
Successfully integrating Privileged Access Management into your office environment requires careful planning and adherence to best practices. It's not merely about deploying software; it's about a fundamental shift in how privileged access is managed and perceived within the organization.
- Identify and Inventory All Privileged Accounts: Before you can secure them, you need to know where they are. This includes human and non-human accounts across all systems, applications, and cloud environments.
- Implement Least Privilege: As discussed, this is paramount. Ensure users only have the minimum access required for their tasks, for the shortest possible duration.
- Enforce Strong Password Policies: Use PAM to manage and rotate complex, unique passwords for all privileged accounts automatically.
- Automate Session Management: Leverage PAM to control, monitor, and record privileged sessions. This provides an audit trail and real-time alerts for suspicious activity.
- Regularly Audit and Review Access: Periodically review who has privileged access and why. Remove access for employees who no longer require it.
- Integrate with Existing Security Tools: PAM should not operate in a silo. Integrate it with your SIEM (Security Information and Event Management), identity management systems, and other security solutions for a holistic view.
- Provide User Training: Educate your privileged users on the importance of PAM and how to use the system effectively and securely.
- Phased Implementation: Start with the most critical systems and gradually expand PAM coverage across your entire infrastructure. This allows for learning and adaptation.
By following these best practices, organizations can maximize the effectiveness of their PAM solution. PAM adds protection to privileged groups that control access across a range of systems, enhancing overall security posture and significantly reducing the risk of a catastrophic breach.
The Future of Privileged Access Management in the Office
The landscape of cybersecurity is constantly evolving, and so too must Privileged Access Management. As organizations embrace cloud computing, DevOps, and remote work, the traditional perimeter dissolves, making PAM even more critical. The future of PAM in the office environment will be characterized by greater automation, deeper integration with other security domains, and leveraging advanced analytics to predict and prevent threats.
Integration with Identity Management
PAM is increasingly becoming an integral part of a broader identity and access management (IAM) strategy. Seamless integration with identity governance, single sign-on (SSO), and multi-factor authentication (MFA) solutions will provide a unified approach to managing all identities, both privileged and non-privileged. This holistic view enhances security, streamlines user experience, and simplifies compliance. The goal is to create a cohesive identity fabric where access is granted based on context, role, and real-time risk assessment.
AI and Machine Learning in PAM
The application of Artificial Intelligence (AI) and Machine Learning (ML) is set to revolutionize PAM. AI and ML can analyze vast amounts of data from privileged sessions to identify anomalous behavior that deviates from normal patterns. This allows for proactive threat detection, even for previously unknown attack vectors. For example, if a privileged user suddenly accesses a system they've never touched before, or performs actions at an unusual hour, AI can flag this as suspicious, triggering alerts or even automatically revoking access until further verification. This predictive capability moves PAM beyond reactive monitoring to proactive threat intelligence, making it an even more formidable defense against sophisticated cyberattacks.
Common Misconceptions About PAM
Despite its critical importance, several misconceptions about Privileged Access Management can hinder its adoption or effective implementation in an office setting:
- PAM is Only for Large Enterprises: While large organizations face complex challenges, even small to medium-sized businesses (SMBs) have critical systems and privileged accounts that need protection. The scale of the solution may differ, but the need for PAM remains universal.
- PAM is Just About Password Vaulting: While secure password management is a core component, PAM is far more comprehensive. It includes session monitoring, least privilege enforcement, just-in-time access, and advanced analytics, going far beyond simple password storage.
- PAM Slows Down IT Operations: When implemented correctly, PAM streamlines access requests and automates credential management, which can actually improve operational efficiency and reduce the burden on IT teams, rather than slowing them down.
- PAM is a One-Time Setup: Cybersecurity is an ongoing process. PAM requires continuous monitoring, policy adjustments, and regular audits to remain effective against evolving threats.
- PAM Replaces All Other Security Tools: PAM is a specialized security layer that complements, rather than replaces, other cybersecurity tools like firewalls, antivirus software, and intrusion detection systems. It's part of a layered defense strategy.
Addressing these misconceptions is vital for organizations to fully appreciate the value and necessity of a robust PAM solution in securing their digital assets.
Real-World Impact: Why PAM Matters for Every Organization
The real-world impact of effective Privileged Access Management cannot be overstated. In an era where data breaches are not a matter of "if" but "when," PAM serves as a critical line of defense. It helps organizations manage and secure access to their most critical systems, applications, and data, which are typically reserved for privileged accounts. Without PAM, an organization is essentially leaving its most valuable digital assets unguarded, making them easy targets for cybercriminals.
Consider the potential consequences of a privileged account compromise:
- Massive Data Loss: Attackers can exfiltrate sensitive customer data, intellectual property, or financial records.
- Operational Disruption: Critical systems can be shut down, leading to significant downtime and loss of revenue.
- Reputational Damage: A breach erodes customer trust and can have long-lasting negative effects on a brand's image.
- Regulatory Fines: Non-compliance with data protection regulations due to lax access controls can result in severe financial penalties.
By implementing PAM, organizations can significantly reduce these risks. It provides the necessary controls to enforce least privilege, monitor all privileged activity, and respond swiftly to suspicious behavior. PAM is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users, ensuring that the digital heart of your office remains protected and resilient against the ever-present threat of cyberattacks. It's an investment in resilience, trust, and the long-term viability of your organization in the digital age.
In conclusion, while "Pam in the office" might evoke a smile for its pop culture reference, the true "PAM in the office" – Privileged Access Management – is a serious and indispensable component of modern cybersecurity. It is the fortress guarding your organization's most critical digital assets, ensuring that only authorized personnel can access the keys to your digital kingdom. By understanding its core principles, implementing best practices, and embracing its evolving capabilities, organizations can significantly enhance their security posture, protect against devastating breaches, and build a more secure digital future. Don't leave your most powerful accounts vulnerable; embrace the power of PAM.
We hope this comprehensive guide has shed light on the vital role of Privileged Access Management in safeguarding your organization. What are your biggest cybersecurity concerns in the office? Share your thoughts and experiences in the comments below, or explore our other articles on strengthening your digital defenses.

Pam - cháu gái tập đoàn may mặc là em bé Việt đầu tiên có loạt ảnh đạt

Privileged Access Management (PAM) in the Cloud
A Closer Look at Identity and Access Management (IAM) and Privileged